0 Results for ""
The Identity Shift: Preparing for a Non-Human Future
Rapid progress in LLM development is moving the bottleneck in the agentic AI market from the agents’ usefulness to the infrastructure required to build and adopt agents securely at scale. Non-human identities (NHI) already outnumber human ones in most enterprise environments and with the rise of autonomous agents, that gap is set to explode. The implications for enterprises are profound; we’re entering an adapt or die moment for organizations large and small.
Agents are dynamic, act independently, and often are created and used before a CISO can manage to find and govern them. Whether it's a shopping assistant checking out on your behalf or a code agent pushing directly to your main branch, the loss of control can be jarring. While agents are helpful and open up an entirely new future for how we work, this future also equips agents with access to sensitive resources. What happens when these agents start flowing into production environments, escalating privileges, pulling data, triggering workflows, or interacting with customers?
All of these challenges create an opportunity for both agent builders and security practitioners:
- CISOs can get ahead of agentic identity challenges, adopt solutions that give them visibility into and control over agents, and position themselves as enablers. Or risk becoming blockers of the most important technological shift of our lifetimes.
- Agent developers can differentiate by defining and implementing agentic security standards in their products. Or risk ceding ground to competitors.
The Risks of Ungoverned Agentic Identities
Adopting unmanaged agents today introduces the compounding challenges of visibility, extensive permissions, and control, which come together to wreak havoc on enterprise environments.
Shadow agents are the new shadow IT. Many agents today are brought in bottoms-up by developers looking to automate their mundane code maintenance or sales reps looking to supercharge their outbound efforts. And we’ve seen this play out before when Github and Slack were being adopted. Security teams eventually had to catch up. Agents are now following the same trajectory. Developers are spinning up LLM-powered agents to automate code maintenance or debugging. Sales reps are building agents for outbound prospecting. These tools are powerful—and often invisible to security.
An organization can’t manage what they can’t see.
This risk compounds when paired with extensive permissions. Many agents today simply ask users for credentials and then operate as if they were the user, after all, the dream of agentic AI is to automate human work. These delegated identities can assume broad permissions. Without visibility into them, security teams will struggle to attribute actions and maintain compliance. And if attackers gain access to the agents, they have a direct path to further escalate access and compromise systems. A shadow agent that adopts a user in the finance department’s permissions could quickly gain access to a public company’s sensitive financial information.
CISOs today lack the control mechanisms required to stop an attack like this. Without guardrails built into agentic systems or control over the authentication and authorization paths the agent is using, they’ll need to rely on reactive approaches to mitigate agent disasters.
A Secure Agentic Identity Posture
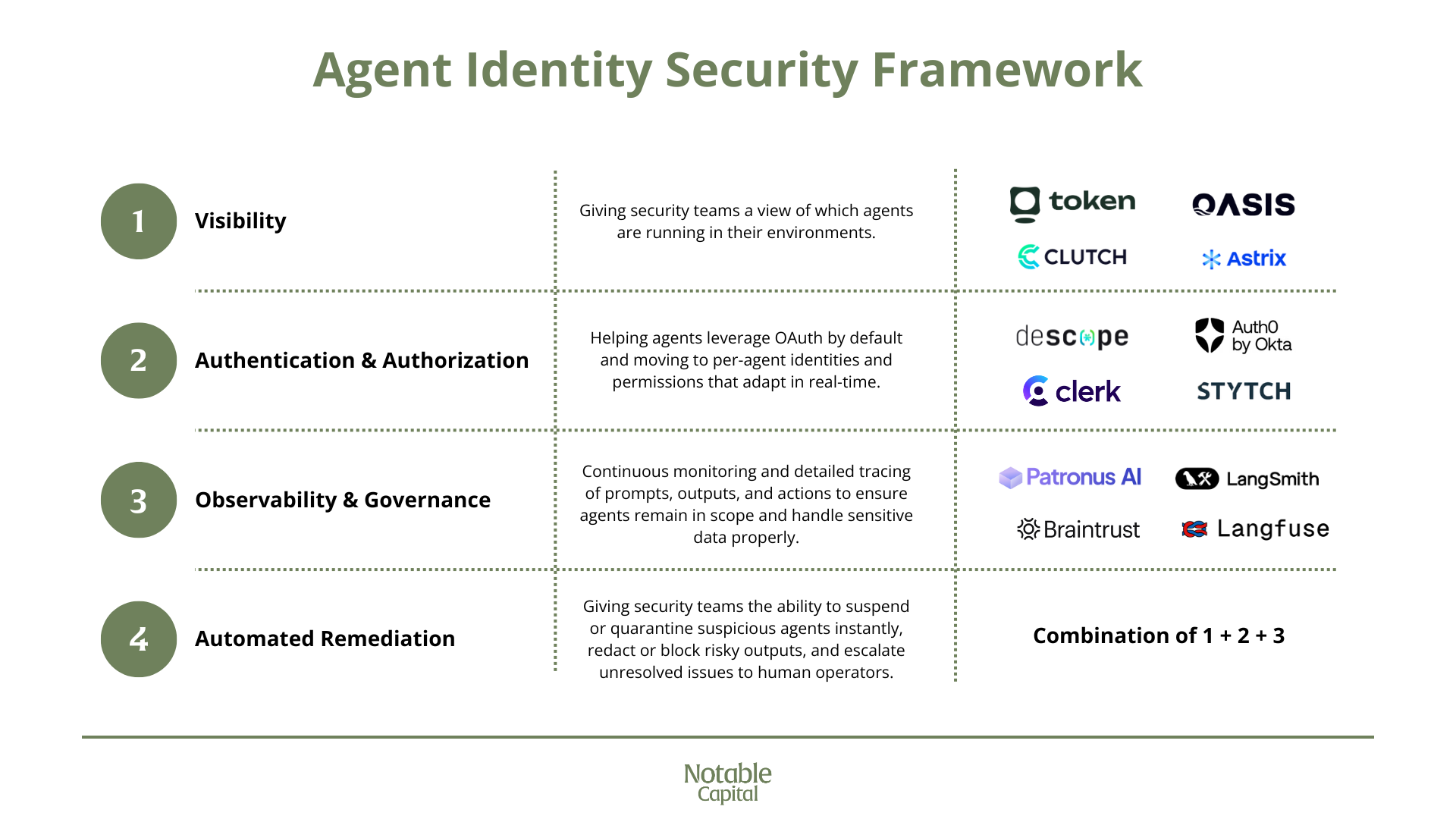
The first step towards securing the use of agents is defining what a secure posture looks like. The CISO of Glean, Sunil Agrawal, has laid out a useful framework to assess the security of the agents:

- Visibility: Security teams need to know exactly which agents are operating within their enterprise.
- Authentication and Authorization: Agents should leverage OAuth by default but move beyond coarse OAuth tokens by assigning per-agent identities and permissions that adapt in real time based on the agent’s role.
- Observability and Governance: Continuous monitoring and detailed tracing of prompts, outputs, and actions to ensure agents remain in scope and handle sensitive data properly. This data should also be used to ensure accountability and compliance with regulations and internal AUPs.
- Automated Remediation: Security teams should have the ability to suspend or quarantine suspicious agents instantly, redact or block risky outputs, and escalate unresolved issues to human operators.
Achieving this posture requires shared responsibility between the agent adopter and the agent developer. It necessitates new approaches to observability, authentication, authorization, and external connectivity.
Visibility
Security teams must gain visibility to know exactly which agents exist within their environments. NHI solutions like Token Security*, Clutch Security, or Astrix Security can help here. By mapping out API keys, certificates, and tokens, they can uncover unmanaged agents and their connectivity to other enterprise systems.
Agent developers will also need to expose more detailed observability data to their customers. Security teams need more than surface-level logs; they must understand the reasoning behind agent actions. Detailed traces of reasoning engines, capturing inputs, outputs, and decision-making contexts, are critical.
Tracing enables security teams to not only see what an agent did but why it took specific actions. This capability is transformative, offering early detection of malicious behaviors or policy violations and providing a path for swift remediation. For instance, if an agent unexpectedly attempts to access sensitive customer information, observability tools can quickly determine if the action resulted from malicious intent, misconfiguration, or a genuine operational requirement.
Authentication and Authorization
To achieve enterprise adoption, agents will need to move from delegated human identities to secure authentication and authorization approaches.
Agents should leverage secure methods such as OAuth 2.0 or JWT tokens, ensuring robust identity verification and dynamic token management. Avoiding static or hardcoded credentials is crucial. Agents should employ frequent credential rotation, limiting the window of opportunity for attackers in case of credential compromise.
Access control is equally important. Implementing granular, least-privilege frameworks, such as role-based access control (RBAC), relationship-based access control (ReBAC), or attribute-based (ABAC) ensures agents only have the minimal permissions necessary to perform their tasks. Developers should continuously audit agent permissions and access controls, quickly correcting overly broad permissions or improper access rights.
Again, agents will need to provide detailed logs and traces to build trust with enterprise security teams. This will allow security teams to detect subtle indicators of compromised agents, such as unusual access patterns or unauthorized attempts to access sensitive data, before they become major security incidents.
Securing Agent Connectivity
The most capable agents today are connecting to internal and external web and SaaS systems to both pull information and take action. That connectivity can take a few forms, but is increasingly centered around API calls, browser automations, and MCPs. Securely adopting agents means ensuring these connections are properly authenticated, monitored, and governed.
Securing API calls falls under the purview of existing NHI platforms and underscores their importance in the era of agents. These platforms ensure that security teams know which APIs their agents are calling and are maintaining hygiene on their connections. Browser automation can be more difficult, but the rise of AI browser clouds like Browserbase, which give developers detailed observability out of the box, can help. By exposing logs and even browser session recordings, they give enterprises the data they need to monitor agents and ensure they’re accessing the broader web securely.
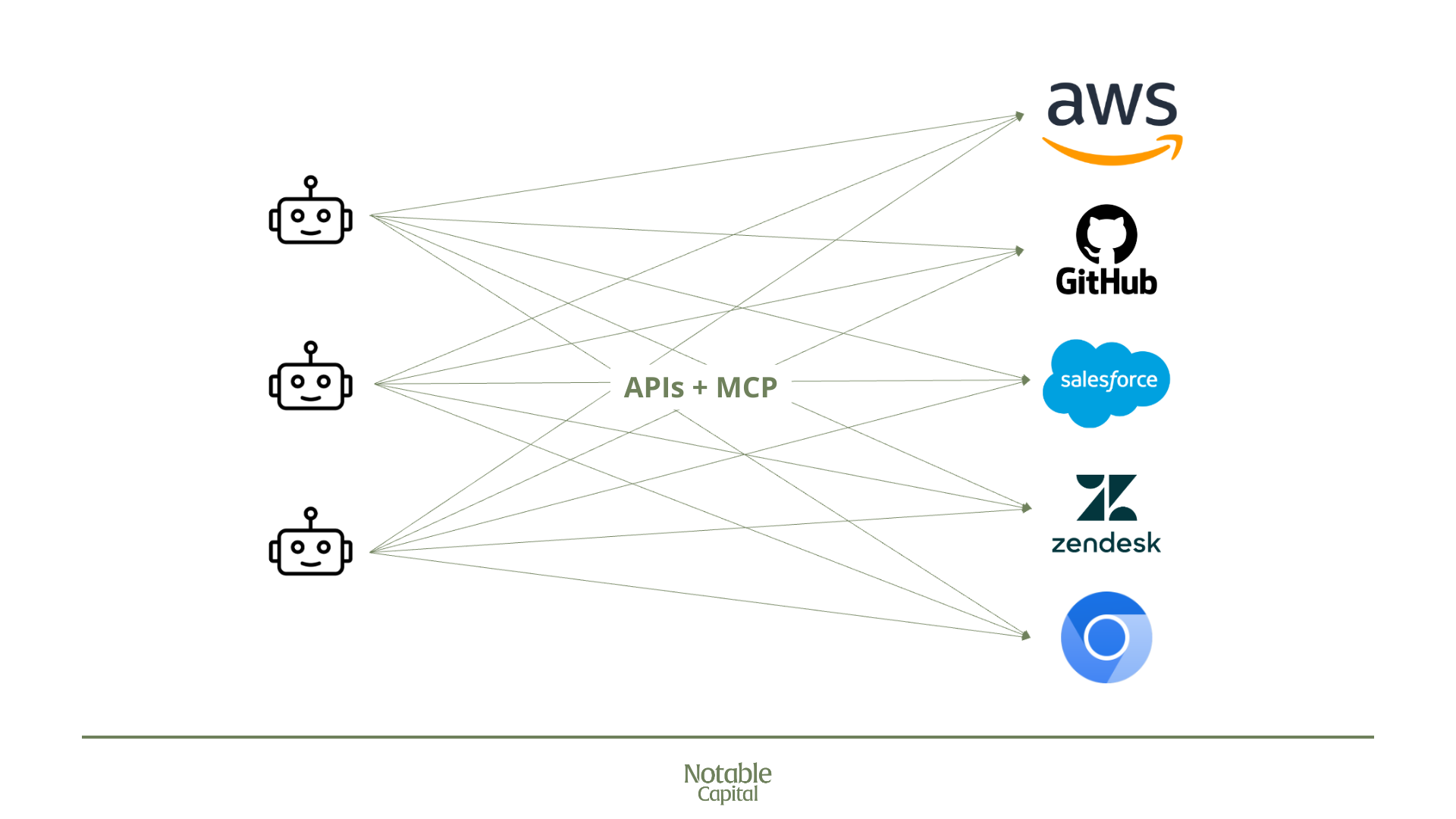
Finally, MCPs continue to gain mindshare as a standardized way for agents to interface with web or SaaS tools. However, many MCPs are being deployed without baseline authentication and authorization requirements. The Anthropic* team recommends implementing OAuth 2.1, but OAuth alone leaves much to be desired, namely fine-grained access control. This gets unruly quickly–hundreds of agents need to connect to dozens of services, the classic NxM problem (visualized below) creating a need for providers like Descope* to enable developers to implement proper auth for MCPs quickly.
The Identity Future is Non-Human
I previously wrote that identity is undergoing a foundational rewrite, moving from a human first model to one defined by software entities. Agents represent a big leap forward, and accelerate this trend. Every new capability we unlock will require better identity infrastructure. Enterprises won’t get the benefits of agentic AI unless they can trust the actors operating inside their systems. And that trust starts with a secure identity layer. Founders working on observability, credential management, behavior tracing, and governance have a critical role to play.
This challenge continues to evolve as agents get better and better. If you’re working on agent security, either as a new startup or a security practitioner, I’d love to hear from you.
*Represents a Notable Capital portfolio company.




